Shipping giant Maersk is one of the big names that has fallen victim to a huge ransomware attack.
The international company's website is offline as the company deals with the impact of the global cyber-attack, Petya.
They have confirmed that some of their IT and communications infrastructure have been affected and they have proactively shut down as a security measure.
 Source: Maerskline website
Source: Maerskline website
The next Maersk ship is due into the Port of Tauranga on Saturday.
A new ransomware campaign referred to as NotPetya, originally reported as Petya, is affecting Microsoft Windows devices globally
New Zealand's National Computer Emergency Response Team – CERT NZ is strongly encouraging NZ businesses ensure their computer networks are protected with software on all devices fully up-to-date.
In many ways, this ransomware is behaving similarly to WannaCry — it infects unpatched Windows devices by exploiting a software vulnerability. If NotPetya infects a device, it will encrypt the hard drive, demanding a ransom is paid to regain access to the device.
A point of difference that this ransomware has from WannaCry is that once a single computer in a network is infected, the program looks for other computers on the network and infects them as well — even when they're fully up to date.
CERT NZ strongly recommends that the ransom is not paid, under any circumstances. At least one email address used to communicate with the attackers has been taken down, and subsequent email addresses are likely to be taken down as well. In this case, this means that you will not be able to recover your files, even if the ransom is paid.
Minister of Communications Simon Bridges was briefed by officials in the Beehive on Wednesday.
'This is the second biggest attack we've seen in recent times of malware,” says Simon.
'There was WannaCry and now this one called NotPetya originating from out of the Ukraine.
'People need to make sure they're protecting themselves. Fortunately it doesn't seem to have come to New Zealand yet. Just as WannaCry didn't either.
'My advice to Tauranga businesses is to make sure you're updating all of your antivirus and other programmes. Whilst that's not going to keep you 100 per cent safe, it will certainly make things safer for you. And the other thing to do is to be very careful when opening emails and attachments.
'If it's a strange name or there's spelling mistakes or something seems weird, don't do it, as it could fill your computer with viruses which could be crippling for you.
'The government has put resources recently into helping people in businesses obtain information and advice so they can find out more particularly if they feel they're at risk.
'These big global attacks don't seem to have got to us. We are seeing roughly an incident a day being reported in NZ. They can have a big impact on business and on every day people going about their lives. So the message is be vigilant, upgrade your software and in particular your antivirus software. '
What to do:
Prevention:
In priority order, these are the technical steps that CERT NZ recommends you take immediately to protect your network.
- Ensure you've patched all Windows systems in your network. In this case, it's particularly important to apply the MS17-010 Microsoft patch. CERT NZ recommends that you apply all security updates to all systems and software.
- Make sure you've backed up your system and have stored your files securely outside your network.
- Make sure that firewalls and anti-virus software is installed, up-to-date, and fully operational.
- Be careful when opening emails and clicking on links – read our phishing information to know what to look out for. These emails could be from anyone, including an email address you're familiar with.
- Ensure staff are aware of this campaign. Remind them to be vigilant about links and attachments contained in incoming emails
EternalBlue vulnerability patch MS17-010
Mitigation:
This is an example of what you may see if NotPetya is attempting to encrypt your files:
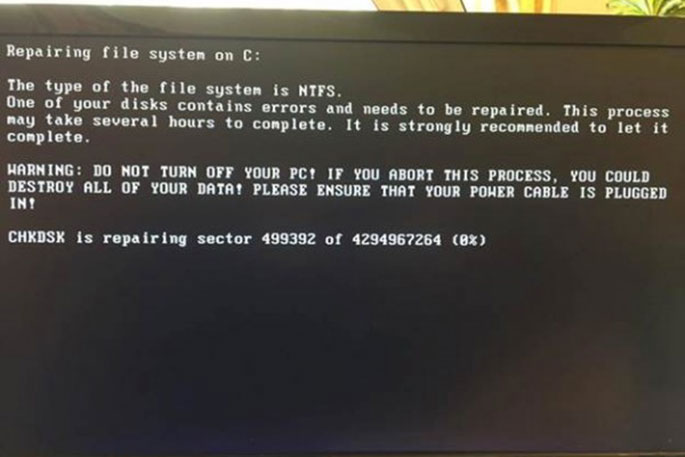 Source: Forbes.com
Source: Forbes.com
If you see this, turn your device off, and don't turn it on again — an IT Specialist may be able to recover your files. If you turn your device back on again and NotPetya encrypts your data, there may be no way to recover it. When this has happened, you'll see something like this on your screen:
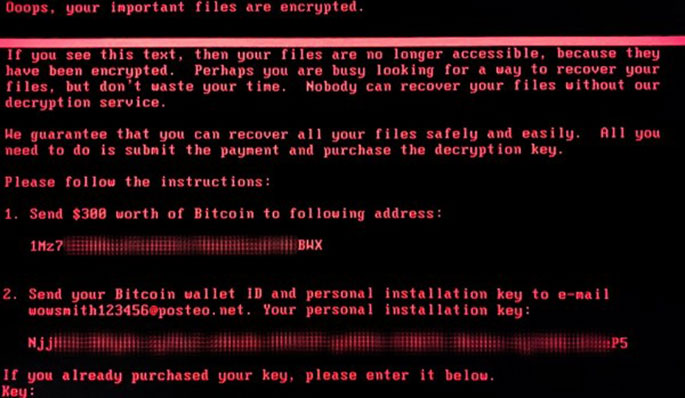 Source: Kaspersky Lab
Source: Kaspersky Lab
More information:
If you require more information or further support, submit a report on to the CERTNZ website or contact CERTNZ on 0800 CERTNZ.



0 comments
Leave a Comment
You must be logged in to make a comment.